|
|
[Home/Nieuws] [Magazines] [Meetings] [Downloads] [Redaktie] [Geschiedenis] |
|
You own it, you hack it! While the exact timings and content of last years cards will be explicitly detailed, you want to be able to keep up with the game and analyze cards from other countries before you get there. In otherwords, if your emulation does EXACTLY what the official version does, your 'card' is therefore the real thing in all respects. Introduction Some of you will find that spent phonecards will make very
secure keys for electric locks. More ambitious hobbyists will want to experiment with true
processor cards. In this case the manufacturer will provide software tools to program the
card. It will be up to the individual to develop their own system. In the meantime the
'inverse reader' can be used to emulate existing chip masks. Tools to do this may be
available from manufacturers of chips for cards. Prices of smartcards can be as While the original scope of this article was to cover the
memory cards or simply put; "dumb cards", it is generally agreed that they are
obsolete. PTT's will continue to use them for years to come, but in the more developed
world, a changeover is likely to occur soon. Holland, Germany and France are almost surely
to be first. However just about every country except the USA has a phonecard with value on
it. (It should be noted here that NYNEX is experimenting with the old-fashioned We will begin with a comprehensive analysis of memory cards and their workings. From the information it will be possible to emulate them. We will discuss security tactics used to discourage this. The sharp reader will learn that is easier to emulate a 'dumb card' than to read/write one. The intelligence is in the cardreader along with all the safeguards, which include things as 'wire detection', 'swallowing the card' and 'blacklisting' abused series numbers. Chipcards Most people think these telephone cards are the much touted 'smartcards'. In fact all prepaid telephone chipcards are just memory cards often referred to in the industry as 'dumbcards'. At present manufacturers often refer to security as using different types of memory, security fuses and special undocumented security features. The Siemens SLE4404 is a good example of a multipurpose memory card. This is quite possibly the German phonecard which has been said to be reloadable up to 100 times. This datasheet mentions this feature, but one must know a 16bit code to get in, which is apparently databased by Telekom. The other option is to blow a certain security fuse and the card is irrevocably single use. Pin 4 is test and pin 8 is that fuse pin. Both become open (not connected) when the card is secured. They are the bottom contacts on eight contact modules. Many one use cards dispense with these contacts altogether. At present there are two major types of memory card on the
market. Both types have their own unique method of marking value and methods of security.
The French type is probably less expensive than the German type mentioned above, been in
use longer and is used in most countries that use chips for phones. Modern readers could
read both of these memory cards and processor cards too. Either through politics or
mistrust of each other's systems, most memory cards are limited The new card adopted the ISO position and uses a NMOS, EPROM technology. 21V +/- 2.5% is applied on the Vpp pin to alter the card. The value is stored as 'units' and the largest card contains 120 and perhaps 10 bonus tiks. There is room for a maximum of 152 units. (see memory map) The total usable memory area, fixed and changeable, is 256bits. Included are country codes, manufacturer codes, the initial value and the last byte contains FF if the card is new. The 'Rest Of the World' version has a slightly different format in the first twelve bytes. While the old versions burned the card in a linear fashion which was provided with the number of units needed, newer versions place more tics than as needed in a particular order determined by the info in the first part of the card. A crypto algorithm determines where the places will be from the series code and possibly other areas of the first 96bits. This algorithm is not known to this author, but is apparently a proprietary one. It purpose is to prevent mass emulation of the cards. It can be assumed that copying one card would allow many 're-uses' until it was 'blacklisted' by the system. One would ofcourse have to change to another phone to use a copy! It is not determined how the cels are updated in France and countries that use the similar system. (Any takers? French police tactics are down right scary!) When a card is used up, there will be remaining 'units'. This is like a LOTTO at its best. Which 16 o 24 or more bits are NOT set out of a field of 152? The apparent key length is 56 bits and the 'LOTTO field' has an astronomically larger range and could act as an extention in a double crypt system. It would appear to be something like DES and perhaps as secure or more so. The NMOS output has levels much like TTL and is compatible to it without any pull-up resistor. The French cards use an active low RST on pin 4. The Vpp is on pin 6 and is +5V while reading and upped to +21V to modify. Pin 2 is R/W and is low (0) unless a modification is to be made. When 1, the Vpp is expected. The CLK is pin 3 and the 'I/O' is pin 7. The system used in Holland is based on the German system
that appeared in 1989. While the card Power-on-reset: If the CLK is 0 and the reset is one, the I/O sources current. A proper reset is RST to 1, a single CLK pulse to 1 and back to 0 and then RST to 0. It has been found the card will reset when the RST falls before the CLK. This may be one of the 'undocumented' security features. The I/O is the clock inverted with the addition of current sourced when the RST is 1. Rise and fall times are very fast and well under 20nS! The sink current is twice the source current as would be expected using equally sized N and P channel fits in a CMOS arrangement. Here is the performance of a typical card. With the RST 1
and the CLK 0, the output will source 4mA at 4V or put another way there will be a one
volt drop if 1k0 is placed from the output to ground. Modifying data: A 'write' is defined as changing a
1 to a 0. An 'erase' is defined as putting all zeros in a lower value field to all 1's. To
perform a write, an RST pulse is generated while the CLK is 0. (this pulse can be as
little as 1uS) The clock is then specified to remain high (1) for 10mS to allow time to
zap the bit. On the actual card, this CLK pulse can also be about 1uS, which allows the
measurement of the time actually required to change the bit. Series number: Chips are made in lots of 100. Each lot has its own number. Through central administration it is possible to monitor fraud and cancel cards that appear to have been used for more than 100 times its value. In general the machine will not care if the number is in range and not in its memory of cards to reject. While not as cleaver as the French method, it will serve to keep criminal and lamer abuse down! Much of the card, like the series number, cannot be altered. There are only 36 'value bits' on most cards. (the older cards had a 1/8 cent subfield that could be written) There are however a total of 80bits that can be set to 0 and stay that way. Trying to write in most 'forbidden' areas will do nothing, but in certain areas the card is frozen (program counter doesn't increment anymore) if a write is attempted. These all appear to be security measures that could be taken to verify a card but it is apparently never done. Future Imperfect Determining card type Processor card emulation In many systems, the 'inverse reader' is used to program the card device. To do this one must know how to answerback with a message saying; "I have more for you". At this point a whole new identity can be loaded or audits conducted. It is likely the speed will be increased to 19.2 or 38.4kb/s for 'security' or time savings. Every 'facility card' is different and either development of your own or leaked knowledge of present types is needed to gain entry to the card itself. You can however reset the card and get an answer and issue it a challenge and get a response. Improper challenges often result in getting an ASCII 'n' (for no?) back. Certain control characters will give predetermined test responses, but only properly framed (and typically 64bit) challenges will produce a normal response. Only by knowing the system of crypto in the card and its keys can you issue a challenge and get the expected response. Ofcourse you must then give the card an answer to it's response and then you may modify its contents! It should be noted at this time, not all cards use crypto. In the industry this is called 'mag stripe emulation'. The German medical card is a fine example of a none secure system. Since the card is readable and writeable in the clear, junks, for instance can get all the dope they need with the help of a hacker. To hack such a system all one must do is monitor the protocol between the reader and card. Inverting the I/O and connecting to the RxD pin of a terminal at 9600 and proper settings will expose the 'conversation'. To do this you need a 'card' and socket to form a sort of breakout box. More sophisticated systems could sererate out what the card says and what the reader says. RSA: End of the road? The cost of this type of card puts this system, for most uses, in the future. On all processor cards, it is the job of the processor to keep secret information on the card. There have been many reports of being able to 'glitch' a card and read out its ROM with keys! Exact details are sketchy and beyond the scope of this article. Besides you are likely to waste quite a few cards before you get results even if using a proven technique. Metal detectors/wire detection and security at the
terminal In other countries, the whole card may be 'swallowed' and held. This will eliminate the need to use sophisticated wire detection methods. The card is entered in the long direction and a trapdoor closes that is supposed to cut off or short out any attached wires. The designers of these systems didn't consider that a type of cable commonly used in consumer products and the like will slip by. It is a tough polyester ribbon with printed conductors. Companies such as AMP will supply them in standard lengths with standard numbers of conductors. A chipcard may need a minimum of five and a maximum of eight conductors. Another approach has been to use microelectronics and build a self-contained emulator. While it may work fine in Germany or Greece it will be rejected by the metal detector in Holland.
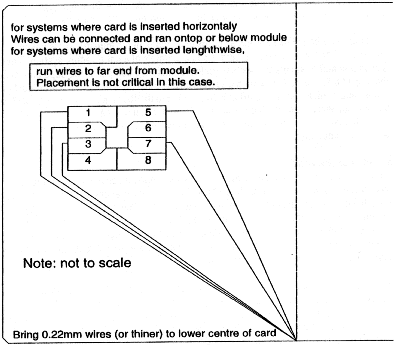
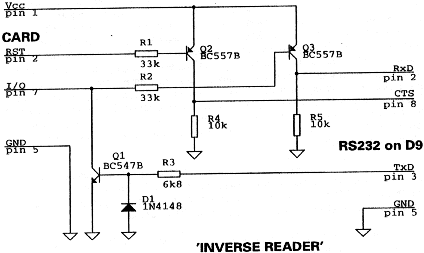
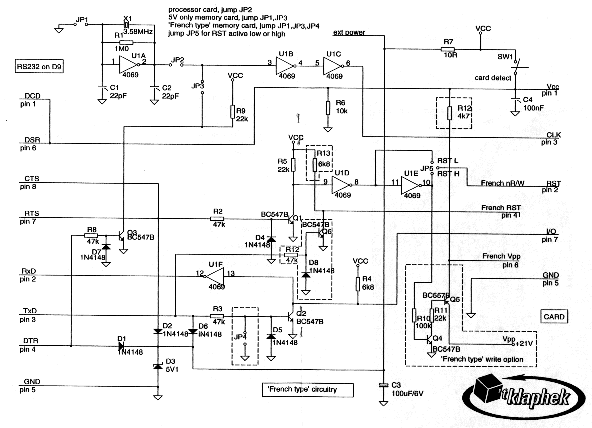
Processor Cards Dumbmouse universal reader/writer (notes on
schematic) To be able to read out and write to memory cards, the 3.58MHz will not be used and shut off (jump JP1), disconnected (open JP2) and DTR will provide for CLK pulses (jump JP3). RTS will be used to reset the card. If it is in the interest to power from the serial port, the position of JP5 should be that RST is inactive when RTS is providing power. During this reset time, the cleaver programmer will set TxD to provide continued power. In the French type phonecards, TxD will provide the actual reset and JP4 will be jumped as TxD will be providing power and preventing an RxD signal otherwise. (A quick note to someone programming: a '0' sent to the serial port produces a positive voltage or 'mark' condition. So when a line is said to be 'providing power', a '0' is being put to that line. Conversely, what comes from the card I/O is inverted before going to the serial port. To power a card at least one and preferably two lines should be 'providing power'. If this is not possible for a certain card, or the crd draws heavy current, additional power must be supplied.) JP5 is to be set so RTS is active for 'most of the time'. This will be fully dependent on the type of card used. For 'active low' resets, as in most processor cards, RST (pin 2) will be connected to U1 pin8, allowing RTS to be active while the card is active. For active high resets, a further inversion available at U1 pin 10 will provide a '0' when RTS is active. To be able to write software, the programmer should have some knowledge of electronics or be within reach of someone who does. Due to possible legal consequences, no software will be provided. Except for writing French cards, simple code has been written to prove the concept. For French cards taking RTS inactive will place +21V on Vpp (pin6) and +5V on the nR/W pin (pin 2), burning the tik and making the I/O go to a '0'. In no case is the I/O port used to input data on a French card. Areas in the dashed lines apply only to French type memory cards and may be omitted if these are not of interest. This circuit is but one example that will cover all aspects
of ISO/IEC 7816. Emphasis was given to a solution requiring no special components or
programming fixtures. Low cost was also a major consideration. The card socket may be
regarded by some as a 'special component'. They are made by ITT Cannon, Omron and Alcatel
among others. This is a new area of hobby so therefore your Inverse reader notes No schematic will be provided for synchronous card inverse readers. The clock must be brought out and all other details are supplied in the text. It is not the intent of this article to be about 'free' calls. How to use a spent phonecard Chipcard Socket Review The above makers also make consumer grade 'less scratching' types where the contacts lower onto the card and only make slight scratches. A further improvement gets devices that lower the contacts directly on the module after insertion and take it up at the least tug of removing the card. In addition to the above makers, these midrange 'commercial grade' sockets are made by Omron, ddm hopt+schuler, Connectral. The 'ddm' device is the superior choice with the Omron SCROJ-002 coming in second place with the others about the same. All are less than 80 gulden one-off. If you must hold the card, try an Omron 3S4YR-SFROJ. It contains a microswitch that detects card entry, a card holding device (stronger than the card!) and a microswitch to indicate a locked down card. Red and green LED's are provided for the user's comfort and convenience and are obviously useful! One-off price: 200 gulden The 'scratching' type are out of the question for any use that involves inserting and removing a card repeatedly. (estimated module life: from 10-100 times for the cheap (phone) cards and perhaps 10 times that for the smartcards with thicker gold plating) There intended use is similar to an IC socket (they all are IC sockets) where a card would be left in place for some time say in a GSM or pay TV decoded. If you want to hobby with these, you'll waste a lot of cards! Well that is what is out there for the hobbyist in a nutshell. I didn't go into the hyper expensive units that 'swallow' the card as they are probably not interesting to the hobbyist. There are many manufactures of these specialised units.
|
|
De informatie in 't Klaphek dient slechts een educatief doel. Gebruik van deze informatie zou strafbaar kunnen zijn. De redaktie wijst iedere verantwoordelijkheid voor gebruik door lezers van de in 't Klaphek opgenomen informatie af. De mening van een auteur weerspiegelt niet noodzakelijkerwijs de mening van de redaktie of uitgever. |
|

 uses a large number of possible security measures, only a few are
actually checked in either country. The card operation and method of storing value are
completely different than the French type. (see memory map) There are 512 possible memory
locations. The card itself contains much of the security. A full rundown of all security
measures will be presented. (see timing diagrams)
uses a large number of possible security measures, only a few are
actually checked in either country. The card operation and method of storing value are
completely different than the French type. (see memory map) There are 512 possible memory
locations. The card itself contains much of the security. A full rundown of all security
measures will be presented. (see timing diagrams)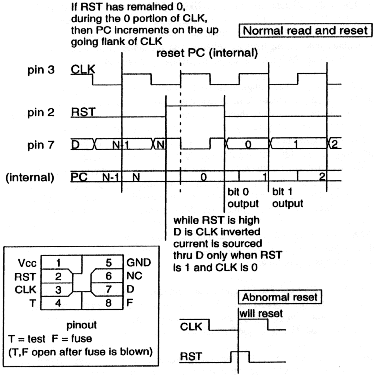 This is the only occurrence of this chip sourcing
current. This chip (like all known CMOS chipcards) normally relies on an 'open drain'
output. It will pull a 1k0 resistor tied to Vcc to 0.5V. (at this point it should be noted
that 6k8 is the standard value used to pull-up the output) On testing about 100 cards, the
propagation delay between the CLK to output into +/-30pF ranged between 18 and 20nS for
the output falling and 33 to 37nS for the output rising with no resistive load. This is
most certainly a security feature.
This is the only occurrence of this chip sourcing
current. This chip (like all known CMOS chipcards) normally relies on an 'open drain'
output. It will pull a 1k0 resistor tied to Vcc to 0.5V. (at this point it should be noted
that 6k8 is the standard value used to pull-up the output) On testing about 100 cards, the
propagation delay between the CLK to output into +/-30pF ranged between 18 and 20nS for
the output falling and 33 to 37nS for the output rising with no resistive load. This is
most certainly a security feature. It has been found to be about 2mS which is far shorter than the worst case
specified. There is probably nothing to do with security here, except the CLK is masked
out during the write period on the newer cards. A read can be performed only if the last
operation was a successful write. (bit changed from 1 to 0) When the CLK is once again 0,
another RST pulse is applied and the CLK is specified to remain 1 for 10mS while all eight
bits of the next lower value field are changed to 1. (In other words you cannot add more
value than you removed. If all the lowerbits are 0, then zapping a higher value bit, you
will restore the same value as each bit in a lower value field is 1/8 that of a higher
value field bit!)
It has been found to be about 2mS which is far shorter than the worst case
specified. There is probably nothing to do with security here, except the CLK is masked
out during the write period on the newer cards. A read can be performed only if the last
operation was a successful write. (bit changed from 1 to 0) When the CLK is once again 0,
another RST pulse is applied and the CLK is specified to remain 1 for 10mS while all eight
bits of the next lower value field are changed to 1. (In other words you cannot add more
value than you removed. If all the lowerbits are 0, then zapping a higher value bit, you
will restore the same value as each bit in a lower value field is 1/8 that of a higher
value field bit!)